
Mobile devices have become companion to human beings. Mobile devices are always within a hand's reach and always remain connected to the Internet. These devices have much larger access to our data (both personal and corporate) as compared to desktops/ laptops. Moreover, these devices can be easily lost/ stolen and can provide direct access to personal information to another person having possession of the device.
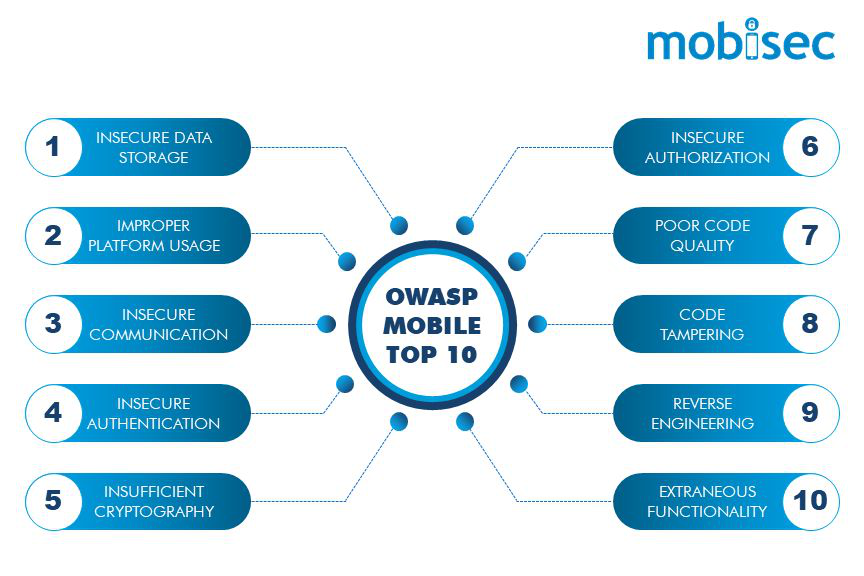
Mobile devices provide various functions or conveniences through mobile apps. There are more than 2.89 million mobile apps on Google Play Store as on 2021. Mobile apps having weak security further increase risk to personal data, privacy, and our money. To strengthen the mobile app security, Open Web Application Security Project (OWASP) has published a list of the ten most frequent vulnerabilities affecting mobile applications called as OWASP Mobile Top 10.
The OWASP Mobile Top 10 framework helps to:
Let’s understand the mobile top 10 risks with a focus on mitigation measures to secure mobile apps.
According to research, 76 percent of mobile applications store data insecurely, putting personal data, financial information, and communication in danger.
Insecure data storage vulnerabilities arise out of poor encryption when the development team assumes that users or malware won’t have access to a mobile device’s file system and uses insecure formats for data storage on the device. Insecure data storage could lead to identity theft, data loss, reputation damage, and fraud, to name a few.
To mitigate the risk, users can avoid saving credentials on the phone and avoid storing personally identifiable information (PII) unless absolutely necessary. For databases, developers may consider using SQLCipher for SQLite data encryption. Mobile app should authenticate the user before granting access to sensitive data. Mobile App Security Testing platform such as mobiSCAN helps to ensure that an app is free from Insecure Data Storage vulnerabilities.
Mobile operating systems or platforms offer a wide range of capabilities, including security controls such as platform permissions, Android intents, and Keychain. The improper platform usage covers misuse of a platform feature or failure to use platform security controls. This vulnerability results from an application's incorrect use of platform features or the failure to implement specific security safeguards allowing them to be utilized as attack vectors or exposing data to attackers.
Unlike the other OWASP Mobile Top 10 vulnerabilities, these flaws are not exclusively the responsibility of the app developer but might result from inadequate documentation or poor communication from the operating system. Hackers abuse an app's permissions by discovering coding weaknesses and exploiting them to obtain access. They can then inject inputs or unexpected execution orders into a device to hack it and steal data.
Improper platform usage vulnerabilities can be avoided by limiting the applications that are allowed to communicate with your mobile application. From a development standpoint, implementing secure coding and configuration practices on the server-side of the mobile application and strictly following platform development guidelines will help mitigate the risk.
Insecure communication is ranked third among mobile vulnerabilities by OWASP. Cyber assaults are possible when sensitive data is sent unencrypted via the public Internet or a mobile carrier network. When data flows via an insecure connection that is not encrypted or uses inconsistent SSL/TLS or uses an older/weaker version of SSL/TLS, a cybercriminal watching the network can hack and abuse any information.
Deploying TLS certificates issued by trustworthy certificate authorities (CA) to protect all communication channels when sending sensitive information, session tokens, and other sensitive data helps to reduce this risk. The use of industry-standard encryption suites and trustworthy signed certificates can further help to mitigate the consequences of these vulnerabilities.
Authentication is akin to verification of identity of a person at the entry gate. Similarly, the identity of a user is verified (or authenticated), before granting access to privileged functions of an app. Due to mobile device’s input form factor, weaker authentication is fairly prevalent in mobile apps. An app having insecure authentication may result in unauthorised access to information or data theft or may cause reputational damage to the enterprise owning the app.
Offline/ local authentication can easily be bypassed on jailbroken devices. Therefore, authentication in mobile apps is recommended at the app’s backend server. Application data should be loaded onto mobile device post authentication only. Any password utilised for authentication should never be stored on the device. Strong authentication protocol and anomaly detection at the backend server are useful to counter automated attacks.
Insufficient Cryptography is the fifth most exploited vulnerability in mobile apps, according to OWASP's Mobile Top 10 list. Cryptography is extremely essential in safeguarding the user's data – especially in a mobile environment where attackers can have physical access to the user's device.
Cryptography or encryption transforms plaintext data into ciphertext, which hides the original content. Decryption is used to recover plaintext data from encrypted text. Encryption can be symmetric (secret-key encryption) or asymmetric (public-key encryption). Algorithms become insecure over time, and so it is imperative to periodically check current best practices and adjust configurations accordingly.
Broken cryptography has personal, business, and technical consequences. These can be classified further into the retrieval of sensitive information from the mobile device resulting in privacy violation, unauthorized access, reputation damage, or IP theft. Here are a few suggestions for mitigating this risk:
Authentication is identifying an individual whereas Authorization is checking that the identified individual is authorized to perform particular action in an app. An attacker login to target app as a legitimate user often having normal/ low privilege. By exploiting poor or missing authorization, attacker executes privileged/ administrative functionalities which are not entitled to him. Insecure authorization may result in destruction of systems or access to sensitive information.
To prevent insecure authorisation— (a) Use backend system’s data to grant roles and permissions to an authenticated user. Don’t rely on information that comes from mobile device or from user request. (b) After successful authentication, immediately perform the authorization to grant access to entitled functions only.
Code quality issues though common within most mobile apps are mostly benign. However, a code quality issue through which execution of foreign code within the mobile app’s address space becomes possible could be risky. The vulnerabilities arising due to poor code quality are exploited by feeding specially crafted inputs. Typical attacks usually exploit memory leaks and buffer overflows.
Code quality issues can be avoided by maintaining consistent coding patterns, sanitising user inputs, and exercising caution while using buffers and unsafe functions. Code review, static code analysis and fuzzing are recommended to discover and fix poor code quality issues.
Code Tampering is modification of an App to create a malicious version. The attacker generally hosts tampered Apps in third-party app stores or tricks users to install the App via phishing attack. This exploitation is quite prevalent because of its ease and control it provides to an attacker.
The tampering could be a direct change in the App binary or replacement of system APIs to intercept and execute malicious code. Its impacts are severe ranging from unauthorised new features, identity theft to frauds for personal/ monetary gain to spying.
A good remediation strategy is to build a capability in the App itself to detect code integrity at runtime. Detecting whether the android device is rooted or not before running the App is also recommended.
Reverse Engineering a mobile app is analysing the app (as obtained from app store) to extract information about its original string table, functions, control flow and source code. Generally binary inspection tools such as IDA Pro, Hopper, otool and strings are used for the purpose. As an example attack scenario, consider the attacker discovers jailbreak detection code in the app and uses this knowledge to disable jailbreak detection by modifying the mobile app binary.
Most mobile apps are susceptible to reverse engineering. Use of obfuscation tools to obfuscate the app code is an effective deterrence against reverse engineering. As part of security testing of mobile app, susceptibility to reverse engineering should be tested.
Extraneous functionality is a functionality that was not intended to be released, however left enabled in an app in public release. For example, a developer may accidentally include a password as a comment or two factor authentication bypassed for testing finds its way in release version.
Extraneous functionality that may provide access to backend systems is often seek by attackers. The attackers examine log files, configuration files, and the app binary to discover hidden switches or any test code. The impact from extraneous functionality includes exposure of how backend systems work and unauthorised execution of high-privileged actions.
Manual code review is most effective to identify extraneous functionality. Automated static and dynamic analysis tools may be useful in identifying log statements and other issues.
The OWASP mobile top 10 framework is platform-agnostic and describes the areas of risk (rather than individual vulnerability) based on its detectability, exploitability, prevalence, and commercial effect. The most recent update released in 2016 remains highly relevant till date. Application of OWASP mobile top 10 framework is recommended to secure the mobile apps.